Supervisory authorities should view supply chains as an asset to use in their enforcement activities instead of an obstacle in their investigations. Let’s use two examples by the Dutch data protection authority (AP) as an example: Locatefamily.com and Clearview AI.
Locatefamily.com
On December 10 2020 the AP fined the website Locatefamily € 525.000,- for violations of the GDPR. Locatefamily.com did not end the violation and bluntly refused to provide information about the identity of the controller and refused to pay the fine. In an interview dated August 26 2024, the AP explained that it made an effort to find out who hosted the website in order to find out the address of the company behind Locatefamily.com but failed in its effort and the AP, practically admitting defeat, closed the case.
The situation looks something like the following diagram:
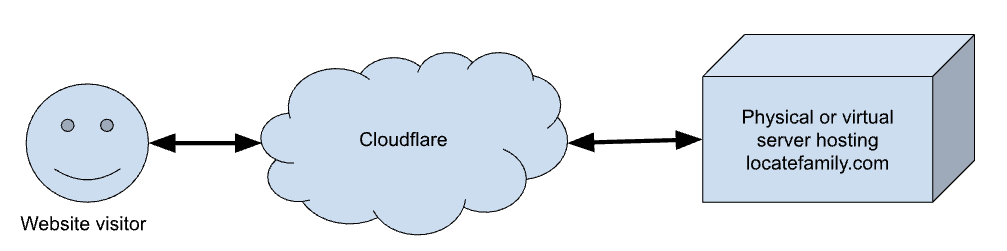 Website visitors don’t connect directly to the web server hosting locatefamily.com, but to Cloudflare. Cloudflare protects their customers from DDOS-attacks,
enforcement by supervisory authorities and other threats. In this case AP contacted Cloudflare with questions about their customer. This is not mentioned in
the interview, but Cloudflare contacted me to ask me to explain to the AP that the AP should use Cloudflare’s abuse form to contact Cloudflare. I presume the AP
tried to contact Cloudflare’s DPO. I did not honor this strange request. But I do have some knowledge about the interaction between the AP and Cloudflare.
In practice Cloudflare doesn’t need to have access to the physical address of a customer.
Website visitors don’t connect directly to the web server hosting locatefamily.com, but to Cloudflare. Cloudflare protects their customers from DDOS-attacks,
enforcement by supervisory authorities and other threats. In this case AP contacted Cloudflare with questions about their customer. This is not mentioned in
the interview, but Cloudflare contacted me to ask me to explain to the AP that the AP should use Cloudflare’s abuse form to contact Cloudflare. I presume the AP
tried to contact Cloudflare’s DPO. I did not honor this strange request. But I do have some knowledge about the interaction between the AP and Cloudflare.
In practice Cloudflare doesn’t need to have access to the physical address of a customer.
If the AP approached the situation with the goal of ending the violation instead of identifying the controller to make sure the fine is paid, the AP could make use of other options.
The AP could have ordered Cloudflare to provide technical information (primarily IP addresses) about the server(s) that Cloudflare is shielding for this customer to find out where they are actually hosted. Additionally the AP could make use of article 58(2)(d and f) to order Cloudflare and possibly any other data processors discovered in the previous step to terminate assisting in the unlawful processing of personal data for this customer. Even if the actual hosting of locatefamily.com itself can’t be touched by the AP the shielding provided by Cloudflare to hide the identity of the controller can be taken away.
Clearview AI
On May 16 2024 the AP fined Clearview AI for violations of the GDPR. While the identity of the controller is known (Clearview AI, Inc., with offices in New York), Clearview AI bluntly refuses to agree that the GDPR applies and has taken no action to remediate the violations or to pay the fine. The AP is well aware of the situation and instead has indicated it will try to hold the CEO personally liable. It is unclear to me what legal mechanisms exist for that approach that are less easy to ignore than the existing fine.
But there are other approaches that are possible too. First lets see how a part of Clearview AI’s supply chain looks like.
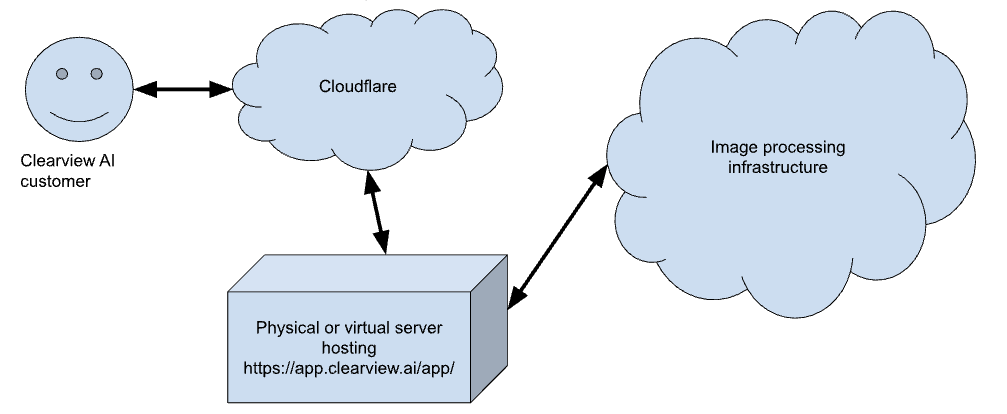
Just like the previous example Cloudflare is used to hide the infrastructure from attacks and supervisory authorities. Given the scale of the data processing by Clearview AI it is reasonable to expect that Clearview AI uses some well known cloud providers for their infrastructure. Based on Gizmodo reporting there are signs that Clearview AI has used at least some AWS and Google infrastructure. However, up-to-date details on the infrastructure hiding behind Cloudflare are not known to me.
As one of the relevant but unsubstantiated arguments of Clearview AI is that they don’t have customers in the EU, the AP might order Cloudflare to provide information about who connects to https://app.clearview.ai/app/, a customer-facing interface from Clearview AI. If any EU-based customers are using the service Cloudflare might ‘see’ their connections. That information might be useful for further enforcement on Clearview AI customers if there are any in the EU.
Additionally the AP could order Cloudflare to provide technical details about the connections they are shielding for Clearview AI. And depending on the complexity of the infrastructure Clearview AI is using some additional orders to other parties providing infrastructure for Clearview AI might be needed to get a reasonable map of the infrastructure used. Depending on the situation that infrastructure can be used to collect (parts of) the fine or the processors like Cloudflare, AWS and Google can be ordered to delete unlawfully processed personal data and to stop any further processing. It is likely that a significant portion of the processors have offices in the EU or even in the Netherlands. This makes it easier to enforce orders to stop unlawful processing for Clearview AI.
Can processors shield controllers from enforcement?
Currently the actions by the AP signal that hiding behind Cloudflare can be an effective tool to avoid consequences of GDPR enforcement. It’s quite obvious that the AP doesn’t want to send that message. Announcing to go after Clearview AI’s CEO is a strong signal. But the AP also chose to publish the fine without being clear that this escalation is a legal and feasible next step. The AP is investigating if it is possible. Time will tell.
And even if it’s possible to hold the CEO personally liable, that doesn’t help with controllers who are successful in hiding behind a processor to hide their entire identity. Locatefamily.com is just a single example, but there are other cases where controllers bluntly ignore data protection authorities (or data subjects who try to exercise their rights) and use infrastructure providers to hide.
Data protection authorities need to learn how to navigate supply chains. If they take a step back from individual complaints and analyze supply chains, data protection authorities might even discover some points where a single enforcement action will improve compliance at many controllers. But even if it’s not for efficiency, the AP should probably look for ways to prevent signaling that some controllers can ignore enforcement action without consequences.