It’s been a while since my last post about Plimus. I have contacted Plimus multiple times since and still haven’t got any response from someone with even a basic knowledge of security. They did however visit my blog and that gave me enough information to figure out that their customer support system stores passwords in plaintext. But what I want to write about is worse.
Let me start by saying that what I am going to write about is not a bug, not an unpatched piece of software and not a subtle design flaw. It’s a feature.
What kind of feature would that be? Imagine you have a webshop and you use Plimus as a payment processor. Your customers will need a Plimus login to handle their payments, and a login to your shop to view their purchase status, or download the content they purchased. Remembering two different account credentials is way too difficult for your customers, so you want to streamline their shopping experience.
I can almost hear you say: “Use OpenID!”, and you would be right. If Plimus would have used some kind of OpenID or OAuth system everybody whould be happy. The customers would have a secure way to use their Plimus login on your webshop. Both you and Plimus could have used standard, free, well tested and opensource software. And you get all kinds of extra features for free, such as retraction of authorization.
Plimus invented their own system described as “Capture Customer Login Credentials”. What this system does is comparable to the IPN system. Every time the shopper changes their account credentials, the webshop can choose to receive a notification. This notification is send as a HTTP POST to a url specified by the webshop. The following information is send:
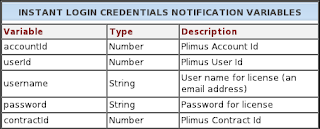
When the webshop receives this message it will add the user to their local database or just change their password to match their new password at Plimus.
I can’t even come close to start describing all the things that are wrong with this, but here is my attempt:
- Users are not notified about Plimus sharing their passwords.
- All information can be send over the internet without SSL, so all passwords can be sniffed.
- There is no authentication, so if I know the url I can create users at the target webshop or change credentials of existing users.
- The webshops themselves have the credentials to login to the customer’s Plimus account with full access.
- There is no procedure for error recovery and credentials can get out of sync.
- I bet you can think of more ways this could go wrong.
If you use Plimus, I have some advice for you:
- Run away and never come back
- If you can’t: complain loudly and publicly about the security issues.
- Can you sue for negligence? And if you work for Plimus: You have both my email address and my phone number. If you have any questions you can use them or leave a comment below.
[Edit] A long time has passed between writing this blogpost and publishing it. The first paragraph contained an inaccurate statement about my contact with Plimus. I have had contact with the Plimus VP & head of marketing who seems to think there are no issues. Someone with technical knowledge should contact me soon.