While discussing Coordinated Vulnerability Disclosure I often experience that people strongly focus on coordinating the vulnerability information with organizations, while the disclosure part is often ignored or even actively discouraged. The last blog I wrote here was actually about a company that argued I had agreed to an enforceable non-disclosure agreement just by visiting their website and reporting a breach. Like my other CVD-related posts, this too is mainly focussed on lessons about the disclosure process. To better understand the decisions I made I feel like it will help if I discuss multiple issues I have reported to the Dutch DPA in the past. While this post lacks an explicit central message, it serves mainly as a brain-dump so people can pick and choose specific points to learn from.
After sending a concept version of this blogpost to the Dutch DPA on september 29’th 2022, exchanging approximately 50 e-mails and an a in-person meeting at the offices of the DPA, the DPA was not able to provide an estimate for the date when they would be able to respond to the issues mentioned below with planned fixes. The bits of information I do have will be included below each chapter and If the DPA chooses to inform me of any aditional measures after publication I will update this blogpost. The DPA did state that they are not aware of any factual error in the blogpost send to them.
Tracking cookies on the DPO conference website, April 2019
On 10 April 2019 the Dutch DPA launched a website announcing the first edition of the conference for data protection officers ‘Dag van de FG’. On the same day I noticed an issue and sent them a direct message on Twitter that stated (translated): The new congres-website contains content from a number of third parties, including fontawesome.com and JQuery.com that state in their privacy policies that they use the collected personal data for their own purposes. I can’t find a relevant privacy policy for JQuery. Both named parties read cookies, I had included two screenshots as evidence and debug information with my message. Showing cookies from multiple third parties being included in HTTP-requests sent when visiting the conference website.
Within 16 minutes the communication department responded stating that my message will be forwarded to the right people. A bit more than two hours later I got confirmation that the external content was removed. I let the DPA know I would be checking the fix and I would be contacting the two organisations to get the already collected personal data removed. Within three hours after contacting the DPA I let them know the issue I reported is fixed and that I let them know the privacy statement needs an minor correction because it erroneously mentions not cookies are used while a session cookie is still used.
After almost a month I managed to get a confirmation from Stripe after being redirected by Fontawesome that unspecified copies of my personal data had been deleted and I couldn’t figure out how to properly contact jQuery and gave up. I believe it should have been the DPAs responsibility to try to make sure the personal data that was unlawfully collected was ereased instead of letting me try to clean up only my own personal data. I have not seen any sign of data subjects being informed about the processing or the breach specifically.
The DPA did not provide me with any information about possible steps the DPA might take to resolve this.
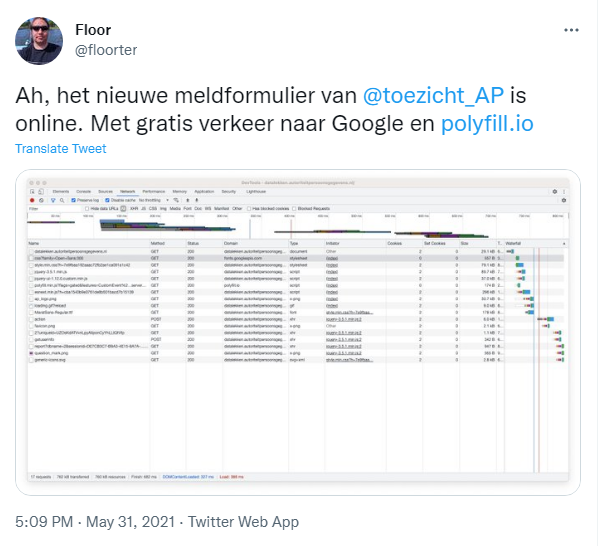
Data leakage from new data breach notification form, May 2021
Under the GDPR data controllers have a requirement to report certain breaches of security of personal data to their national data protection authority. The Dutch DPA provides a web form where breaches must be reported. On 31 May 2021 the DPA launched an entirely new version of this form created by Berkeley Bridge, a company from Alphen aan de Rijn. On the same afternoon as the new form launched I noticed two issues with the new form, described earlier in a blogpost by my colleague: https://www.privacycompany.eu/blogpost-nl/een-spannend-nieuw-meldformulier-datalekken [in Dutch].
First: the form leaks the IP address of the computer filling in the breach notification form and the fact that they are filling in the form to Google and the Financial Times. While Google can probably relate IP-addresses to the individual persons behind it in many cases, for the Financial Times it can be interesting enough to deduce what controller is reporting a breach. For larger organisations who own their own IP-ranges, the link between IP-address and organisation is a matter of public record. Therefore the DPA violated the confidentiality of the reporting process (for both full and partially filled in forms) even if the contents of the reporting remained confidential and even if it’s not always possible to link the data to an individual data subject.
Secondly, while filling out the breach notification form, the DPA collects concept answers while the form is not explicitly submitted. Reporting a breach can be quite complicated and the person filling out the form can often require additional information from within the organization while filling in the form. It is therefore important that the person filling in the form has the ability to involve all stakeholders before submitting the information to the DPA. Without informing people the DPA silently collects partial responses. The DPA does not rule out that information that is collected before explicitly submitting the form can be used for enforcement purposes.
There are a few factors why I didn’t report privately before publishing:
 Public disclosure should not result in additional abuse or breaches. It’s not an exploitable vulnerability.
I believe the DPA was already under an obligation to inform the data subjects about the processing before I discovered it.
Public disclosure for vulnerabilities that are actively exploited in the wild seems to be the norm in the security industry and this situation is analogous to that. By warning people who have to use the form I’m allowing them to reduce risk.
Public disclosure should not result in additional abuse or breaches. It’s not an exploitable vulnerability.
I believe the DPA was already under an obligation to inform the data subjects about the processing before I discovered it.
Public disclosure for vulnerabilities that are actively exploited in the wild seems to be the norm in the security industry and this situation is analogous to that. By warning people who have to use the form I’m allowing them to reduce risk.
The next day the DPA responded on Twitter that the issue was resolved. Without any specification about what the DPA considered to be the issue and what about is has been resolved. I have asked to clarify if the data that has been send to Google and the Financial Times has been deleted.
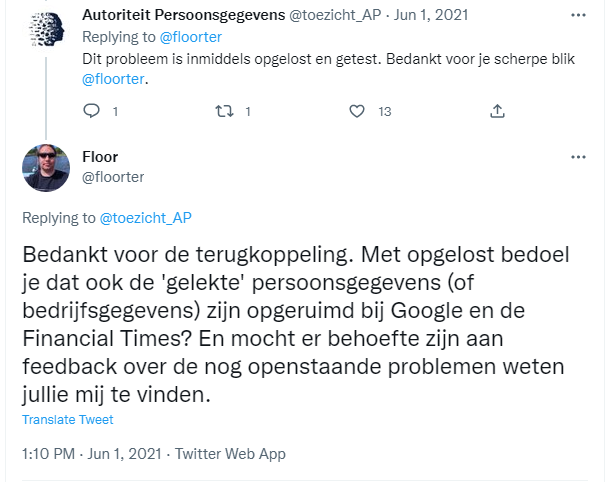 At the moment of writing I have received no response from the DPA on this question.
At the moment of writing I have received no response from the DPA on this question.
Only after a law firm who have a well known privacy branch together with one of my colleagues started asking questions and involved me in CC did I receive some additional information at the end of August 2021. The DPA did request Google and the Financial Times to delete the data they received. I have seen no confirmation that the data is actually deleted. After explicitly stating that my personal data was involved in the breach and that if the DPA was informing data subjects I would like a copy of that message the DPA explained that they did inform all data subjects where they had contact details. Ignoring the fact that they have my contact details and didn’t send me a notification and that the DPA has other means to contact data subjects, like their website. I have interpreted the communication from the DPA, refusing to respond to me directly and giving an obviously untrue explanation for not informing (all) data subjects as a not so subtle hint that they don’t want to communicate with me.
In the same e-mail the DPA also explained that the privacy statement of the form will be updated soon to explain how the form is functioning. At the time of writing, over a year later, the privacy statement of the form is still not updated to reflect the processing. The explanation of the form even states “Het bewaren van de sessie betekent niet dat u de melding naar de AP heeft verzonden.”. This false statement means that saving the (possibly incomplete) form to a local file doesn’t mean the report is send to the DPA. While the form is still sending partial form data to the DPA and especially before saving a form to a local file the last pieces of the form that have not been send to the DPA have to be send to be included in the file. That’s how the form is build. The DPA is still not transparent about any obstacles that would prevent them from using partial form data that is secretly collected in enforcement actions.
Additionally the DPA explained that they have a coordinated vulnerability disclosure policy where they’d prefer me to report any subsequent issues I find. However the terms of the policy would prevent me from revealing any information about issues the DPA hasn’t fixed yet, like the issues described above and the DPA reserves the possibility that there will be ’legal consequences’. To me such terms are completely unreasonable and absurd and I won’t pretend I agree to a potentially indefinite non disclosure agreement for reporting issues.
Update: Through the lawfirm mentioned above I know that Google confirmed on August 20 2021 that the data they collected has been removed and the Financial Times confirmed on Juli 23 2021 that they never stored the information they received. The DPA never communicated this to me. The privacy statement still contains untruthful information that suggests the form isn’t collecting any information not purposefully submitted.
Lack of transparency about international transfers, April 2022
Dutch journalist Sjoerd Hartholt worked on an article about undocumented and intransparent international transfers (https://www.agconnect.nl/artikel/gemeenten-hebben-geen-benul-van-data-doorgifte-aan-vs ) while discussing the legal requirements with me. I explained that international transfers should be documented in the registry of processing and should be communicated to data subjects. For the article I proposed taking some obvious processing with international transfers, like the use of social media and Google Analytics and compare the reality with available registries and/or privacy statements. When the question came up how such registration should look like, I decided to take the Dutch DPA’s social media use and show Sjoerd how it’s registered in their (published) registry of processing and privacy statement.
When I looked at the DPA’s registry and privacy statement the international transfer was not mentioned.
I decided to inform the DPO of the DPA privately before publication on 25 April 2022. I was frustrated by the communication after my previous reported issue and wanted to try if private reporting would get a better response. Four days later I got a response from the DPO. She addressed the right people internally and would get back to me. On 17 May I noticed a new version of the registry was published online yet the international transfers were still not mentioned. I let the DPO know about this. On 6 July, more than two months after my initial mail and after the journalist had asked his questions to the DPA I got a response.
The DPA will wait for guidance from the EDPB about social media use by government organizations before determining if international transfers should be registered in their registry of processing. This response raises questions about two conflicting roles of the controller who is also a supervisory authority who as a controller decides to postpone it’s own compliance while the supervisory authorities are jointly working on guidance that has not been announced publicly anywhere before and since. I’m also not convinced reporting issues privately has any positive impact on the response by the DPA.
The response itself is interesting as an example for other controllers. The DPA sees room to refrain from informing data subjects about international transfers (art. 13(1)(f) or 14(1)(f) of the GDPR) and from noting the transfers in their processing registry (art 30 of the GDPR). I’ll leave it to others to figure out the legal reasoning behind this.
No new response has been given by the DPA.
Google Analytics on DPO conference website, June 2022
On 9 June 2022 the Dutch DPA announced the next national DPO conference on a special conference website. On that website the DPA used Google Analytics together with some other content hosted by different controllers leading to similar issues like the ones discussed in earlier incidents. However, the circumstances made the use of Google Analytics quite remarkable. Several supervisory authorities have concluded that the use of Google Analytics in any reasonable fashion is unlawful because of the international transfer of personal data that’s not sufficiently protected. The Dutch supervisory authority has been less clear in its communication. The DPA does not adopt it’s colleagues’ conclusions but published a statement that it’s still doing its own investigation. This has created so much confusion that I have encountered quite a few people claiming the Dutch supervisor claims the use of Google Analytics is still allowed in the Netherlands. Obviously the use of Google Analytics by the DPA itself on a newly launched website sends a strong signal. So immediately after noticing it I drew the conclusion that apparently the Dutch DPA signals the Google Analytics is allowed.
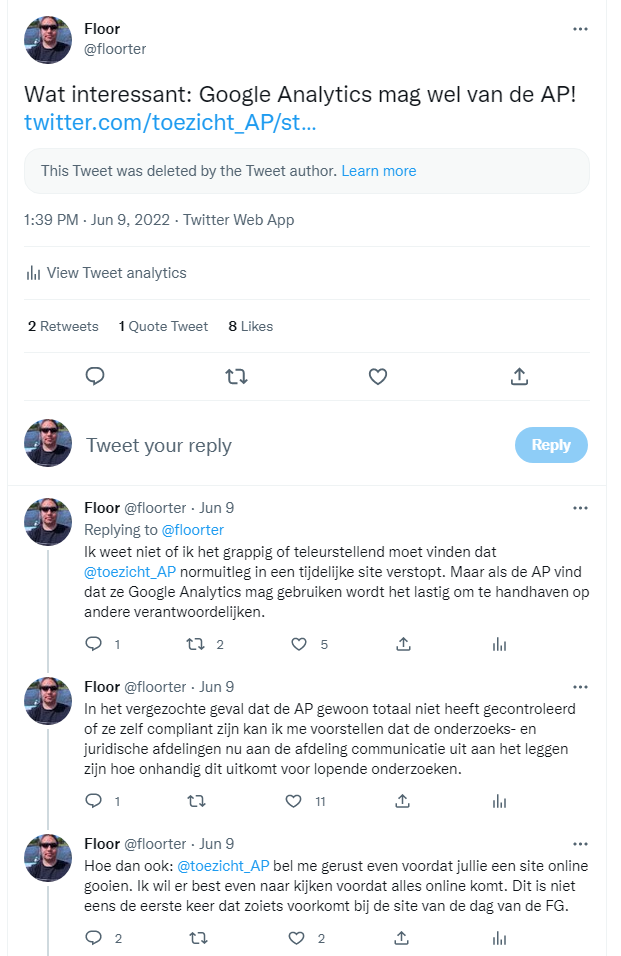
The DPA was quick to react by announcing that it was not the intention and that the site was taken offline.
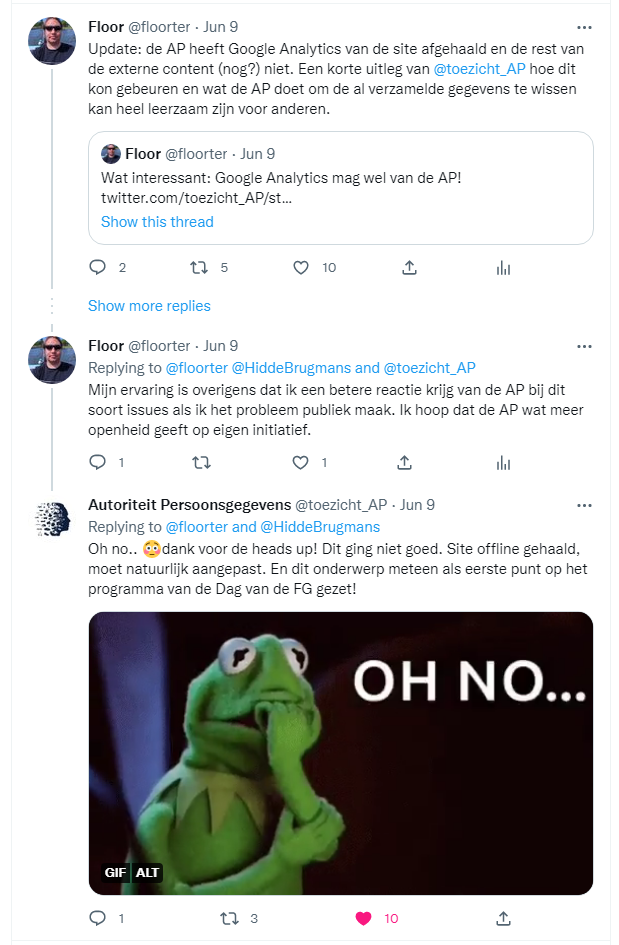
Like similar incidents before, at least two questions remain: are data subjects informed about the processing and will the personal data collected by third parties be deleted? The DPA did announce to address the issue at the first day of the conference, however on 23 august the DPA also announced the DPO conference will be delayed to an unspecified moment. I have heard from one person that the DPA did send a letter explaining the breach to that one person. It is not known to me what the logic was behind determining who to send this letter. My personal data was clearly affected, the DPA knows my personal data was affected and has my contact details because I reported the issue and I didn’t receive such a letter. As far as I know the DPA did not indicate that all collected personal data has been deleted. I would suggest the DPA to inform all data subjects and maybe even publish a short report on their website for all data subjects where contact details are not available and to serve as an example on how to deal with such incidents. It can be helpful for other controllers to learn from incidents like this.
Update: While the point itself might be a bit academic, the DPA as still refused to reverse the decision not to send me a copy of the letter send to affected data subjects. The DPA did inform me that Google has confirmed in the beginning of October 2022 that they have deleted the personal data they received in this context. I have suggested the DPA to communicate about the incident more publicly because it also demonstrates how to deal with incidents like this even though it’s not a perfect example.
Dutch DPA using OpenText to send e-mails and DMARC miscommunication, August 2022
On 8 august I noticed one email message from the Dutch DPA that contained a confirmation of a complaint I filed that ended up in my spam folder. After some digging I found out that the DPA is using the company OpenText to send the email and the DMARC configuration did not allow OpenText to send emails on behalf of the DPA. Because I reasoned that there was no risk of abuse and it is not a security vulnerability I reported the issue publicly on Twitter.
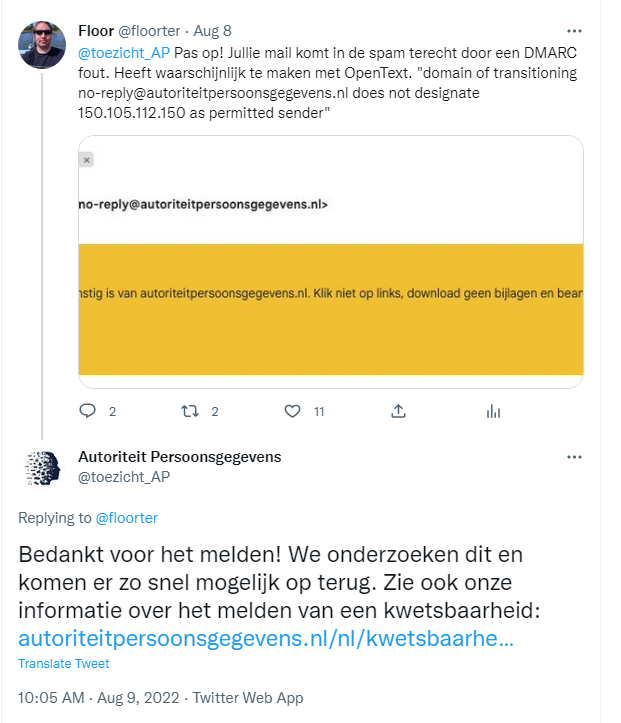
Additionally I e-mailed the DPO of the DPA stating that the use of OpenText meant an international transfer of personal data that was not registered in the registry of processing and was not communicated to data subjects. Besides a confirmation that my mail was received I have not received a reply from the DPO about the contents of my report.
The next day the DPA responded on Twitter, stating they would get back to me as fast as possible while also referring me to their CVD policy. I explained why I believe this issue was out of scope and why I refused to agree to the CVD terms that contain a requirement to not disclose my findings for an indeterminate amount of time. I did contact the CISO of the DPA by email and explained the issue and that while I agree to the principles of CVD I refused to agree to the NDA-terms the DPA requires for reporting. On 22 September I got confirmation that the DMARC issue was solved. OpenText is now authorized to send emails on behalf of the Dutch DPA. People affected, where an email likely ended up in a spam folder did get a new email explaining there was a misconfiguration together with the original email, so data-loss was avoided.
The story is more complicated concerning the international transfer. At an unspecified time in the future, the DPA will update its privacy policy and registry of processing to reflect the international transfer. This will make sure people who file new complaints are informed about the transfer. However people who have filed a complaint in the past will likely not keep up to date with changes in the privacy statement of the DPA and will therefore not be informed about the transfer. The DPA disagrees with this conclusion and argues that the data subjects will be informed indirectly by including the international transfer in the registry of processing. Data subjects be warned: apparently you need to proactively keep checking the registry of processing of all controllers to be properly informed about their processing. When asked explicitly why the DPA did not include a mention of international transfers in the email they sent out about the misconfiguration the DPA responded that they consciously made the choice not to inform the data subjects in the e-mail and that including a paragraph about the registry of processing would create confusion. The DPA argues that because of the adequacy decision for the UK the transfer risk isn’t high. I have not been able to determine on what legal basis the decision to not inform a part of the data subjects about the international transfer is based.
The transfer itself is also interesting for people with interest in GDPR compliance. The DPA stated that the servers of OpenText used for the processing are located in the UK. However, people working with GDPR compliance in international transfers know that international transfers are much more complicated than just the physical location of servers. For example, support from third countries can also constitute international transfers. And OpenText provides support from various countries and has offices in many countries like the U.S., Russia, Brazil, China and South Africa. It would be great to see how the DPA managed to assess the compliance of this situation. Anyone filing a complaint can request the DPA to provide the safeguards for the international transfers, but it would be way better if the DPA could publish a write up to explain how they tackled this.
Update: On September 15 2022 the DPA send an e-mail to the people who’s e-mail was affected including a copy of the original e-mail that was affected. The DPA did explain to me that the DPA has chosen not to inform those data subjects in that e-mail about the international transfer of their personal data because that would be confusing to them. The DPA did explain to me that they will inform data subjects by updating they registry of processing (they did on October 26 2022). When I confronted the DPA that silently changing a registry of processing might not be an effective way to inform data subjects, the DPA clarified it would also update it’s privacy policy. The DPA did not tell me when they where planning to do so or respond to my concerns that it might not be an effective method to inform people who have been affected an have been misinformed in the past.
Conclusions
My main feeling after reporting a few issues to the DPA: the DPA is relatively quick to respond but has much to improve in communication. I hope that the DPA learns that repeatedly excluding me from information provided to other affected data subjects does not motivate me to report issues privately. The DPA’s CVD policy needs a re-work to be better aligned with the intent of CVD: collaboration to fix issues and communicate about the issues so others can learn from it and improve themselves too. Much of what I have written here should have been written by the DPA. I hope they will do that in the future and maybe even give credit to the person reporting issues.
Update: While a few issues are resolved after giving the DPA a copy of this blogpost some significant issues remain. Most importantly is the fact that the DPA, despite the obvious best efforts of the people I had contact with, is nowhere near ready to handle CVD reports. It took the DPA close two months months without being able to provide an estimate of what will be fixed (not counting the years since the original reports) while the DPA’s own CVD policy promises they will provide a date for a fix within 3 days of reporting an issue. Maybe even more important: even the things the DPA is doing right, could serve as an excellent example for others and where there might even be a legal obligation to inform data subjects, the DPA seems to remain reluctant to communicate openly. That reluctance is a strong indication to me that the DPA is not ready and willing to properly adopt a CVD policy. I would strongly suggest a talk by Katie Moussouris about issues by this to anyone wanting to understand more.